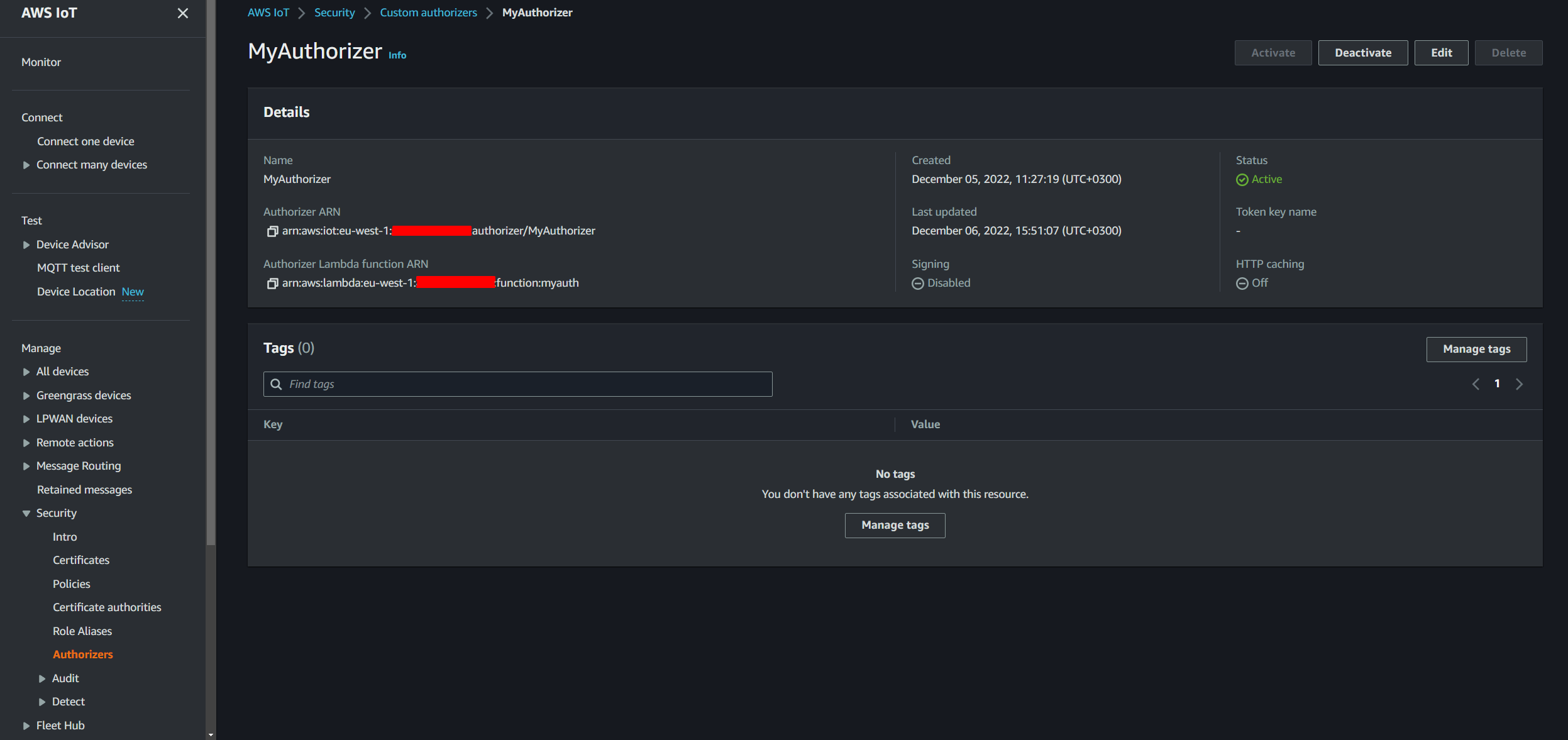
SSH login IoT username and password is a critical topic for anyone managing Internet of Things (IoT) devices. As IoT devices become increasingly integrated into our daily lives, securing access to these devices is more important than ever. Whether you're a system administrator, a developer, or simply a tech enthusiast, understanding how to securely log in to IoT devices using SSH is essential. This article will guide you through the process, ensuring that you can access your devices safely and efficiently.
IoT devices often operate in environments where security is paramount. From smart home devices to industrial sensors, the ability to remotely manage these devices via SSH is a powerful tool. However, with great power comes great responsibility. Misconfigurations or weak credentials can lead to unauthorized access, potentially compromising sensitive data or even entire networks. Therefore, mastering SSH login practices is not just a technical skill but a necessity for safeguarding your IoT infrastructure.
In this guide, we will delve into the intricacies of SSH login for IoT devices. We'll cover everything from basic setup to advanced security measures, ensuring that you have a comprehensive understanding of how to manage your devices securely. By the end of this article, you will be equipped with the knowledge to implement best practices for SSH access, protecting your IoT ecosystem from potential threats.
Table of Contents
Introduction to SSH and IoT
SSH, or Secure Shell, is a cryptographic network protocol used for secure data communication, remote command execution, and other secure network services between two networked devices. It is widely used for managing systems and applications remotely, ensuring that the data transmitted between the client and server is encrypted and secure.
IoT, or the Internet of Things, refers to the network of physical devices, vehicles, home appliances, and other items embedded with sensors, software, and connectivity, enabling them to connect and exchange data. IoT devices are often deployed in environments where remote management is necessary, making SSH a vital tool for administrators and developers.
The combination of SSH and IoT creates a powerful synergy, allowing for secure and efficient remote management of devices. However, the unique challenges of IoT environments, such as limited processing power and memory, require careful consideration when implementing SSH. Understanding the basics of both SSH and IoT is crucial for anyone looking to manage these devices effectively.
Setting Up SSH on IoT Devices
Setting up SSH on IoT devices involves several steps, from installing the necessary software to configuring the server. The process may vary depending on the specific device and operating system, but the general principles remain the same.
First, ensure that your IoT device supports SSH. Most modern IoT devices come with SSH pre-installed, but if not, you may need to install it manually. For devices running Linux-based operating systems, you can typically install SSH using the package manager. For example, on a Raspberry Pi running Raspbian, you can install SSH by running the following command:
sudo apt-get install openssh-serverOnce SSH is installed, you need to configure the server. This involves editing the SSH configuration file, usually located at /etc/ssh/sshd_config. Here, you can set various options, such as the port number, authentication methods, and access restrictions. It's important to configure these settings carefully to ensure that your SSH server is secure.
Securing SSH Access
Securing SSH access is crucial for protecting your IoT devices from unauthorized access. There are several measures you can take to enhance the security of your SSH server.
Using Strong Passwords
One of the simplest yet most effective ways to secure SSH access is by using strong passwords. A strong password should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using common words or easily guessable information, such as your name or birthdate.
Consider using a password manager to generate and store complex passwords. This not only helps you create strong passwords but also ensures that you don't forget them. Additionally, regularly updating your passwords can further enhance security.
Implementing Key-Based Authentication
Key-based authentication is a more secure alternative to password-based authentication. It involves generating a pair of cryptographic keys: a private key, which you keep on your local machine, and a public key, which you upload to the IoT device.
To set up key-based authentication, first generate the key pair using the following command:
ssh-keygen -t rsa -b 4096Next, copy the public key to the IoT device using the ssh-copy-id command:
ssh-copy-id username@iot-device-ipFinally, configure the SSH server to allow key-based authentication by editing the /etc/ssh/sshd_config file and setting the following options:
PubkeyAuthentication yes PasswordAuthentication noThis disables password-based authentication, ensuring that only users with the correct private key can access the device.
Troubleshooting SSH Issues
Despite careful setup and configuration, you may encounter issues when trying to log in to your IoT device via SSH. Common problems include connection timeouts, authentication failures, and permission errors.
If you experience a connection timeout, ensure that the SSH server is running and that the correct port is open. You can check the status of the SSH service using the following command:
sudo systemctl status sshFor authentication failures, double-check your username and password or SSH key. Ensure that the username is correct and that the password or key matches the one configured on the server. If you're using key-based authentication, verify that the public key is correctly added to the ~/.ssh/authorized_keys file on the IoT device.
Permission errors often occur due to incorrect file permissions. Ensure that the ~/.ssh directory and the authorized_keys file have the correct permissions:
chmod 700 ~/.ssh chmod 600 ~/.ssh/authorized_keysBest Practices for SSH Login
Implementing best practices for SSH login can significantly enhance the security of your IoT devices. Here are some recommendations:
- Use Non-Default Ports: Change the default SSH port (22) to a non-standard port to reduce the risk of automated attacks.
- Limit User Access: Restrict SSH access to specific users or IP addresses using the
AllowUsersorAllowGroupsdirectives in the SSH configuration file. - Disable Root Login: Prevent direct root login by setting
PermitRootLogin noin the SSH configuration file. - Enable Two-Factor Authentication: Add an extra layer of security by enabling two-factor authentication (2FA) for SSH access.
By following these best practices, you can minimize the risk of unauthorized access and ensure that your IoT devices remain secure.
Common SSH Security Threats
While SSH is a secure protocol, it is not immune to threats. Understanding common SSH security threats can help you take proactive measures to protect your IoT devices.
Brute Force Attacks: Attackers may attempt to gain access by systematically trying different username and password combinations. To mitigate this risk, use strong passwords and consider implementing rate limiting or fail2ban to block repeated login attempts.
Man-in-the-Middle Attacks: These attacks occur when an attacker intercepts communication between the client and server. To prevent this, always verify the server's fingerprint before connecting and use SSH keys for authentication.
Exploiting Vulnerabilities: Software vulnerabilities in the SSH server or client can be exploited by attackers. Regularly update your SSH software and operating system to patch known vulnerabilities.
Advanced SSH Configurations
For those looking to further enhance the security and functionality of their SSH server, advanced configurations are available. These include setting up SSH tunnels, configuring port forwarding, and using SSH multiplexing.
SSH Tunnels: SSH tunnels allow you to securely forward traffic between two networks. This can be useful for accessing internal services or bypassing firewalls. To create an SSH tunnel, use the -L or -R options with the ssh command.
Port Forwarding: Port forwarding allows you to redirect traffic from one port to another. This can be used to access services running on different ports or to bypass network restrictions. Configure port forwarding in the SSH configuration file using the LocalForward or RemoteForward directives.
SSH Multiplexing: SSH multiplexing allows you to reuse an existing SSH connection for multiple sessions, reducing the overhead of establishing new connections. Enable multiplexing by adding the following lines to your SSH configuration file:
ControlMaster auto ControlPath /tmp/ssh_mux_%h_%p_%r ControlPersist 4hSSH and IoT: Future Trends
As IoT technology continues to evolve, so too will the role of SSH in managing these devices. Future trends may include the integration of SSH with emerging technologies such as artificial intelligence (AI) and machine learning (ML) to enhance security and automate management tasks.
AI-Driven Security: AI and ML can be used to detect and respond to security threats in real-time, providing an additional layer of protection for IoT devices. By analyzing network traffic and user behavior, AI-driven systems can identify anomalies and take proactive measures to prevent attacks.
Automated Configuration Management: Tools like Ansible, Puppet, and Chef can be used to automate the configuration and management of SSH servers on IoT devices. This reduces the risk of human error and ensures that devices are consistently configured according to best practices.
Quantum-Resistant Cryptography: As quantum computing becomes more prevalent, the need for quantum-resistant cryptographic algorithms will increase. Future SSH implementations may incorporate these algorithms to ensure long-term security.
Conclusion and Call to Action
In conclusion, mastering SSH login for IoT devices is essential for anyone responsible for managing these devices. By understanding the basics of SSH and IoT, setting up and securing SSH access, and following best practices, you can ensure that your devices remain safe from unauthorized access.
We've covered a wide range of topics in this guide, from setting up SSH on IoT devices to advanced configurations and future trends. However, the world of IoT and SSH is constantly evolving, and staying informed is key to maintaining security.
We encourage you to continue exploring this topic and to share your experiences with others. If you have any questions or insights, feel free to leave a comment below. Additionally, consider reading our other articles on IoT security and management to further enhance your knowledge. Together, we can build a more secure and connected future.
You Might Also Like
How To Use SSH On IoT Devices Anywhere With AndroidHow Do I Secure My Raspberry Pi Remotely? A Comprehensive Guide
Remote Raspberry Pi And IoT Device Update Download On Windows
1965: The Year Of The Snake - Insights, History, And Cultural Significance
Best Remote Access IoT Behind Router For Android Devices
Article Recommendations
- Unraveling The Life And Career Of Mike Singletary How Old Is Mike Singletary
- The Ultimate Guide To Mydesi Net Mms Unlocking The Secrets Of Indian Erotica
- Judge Jeanine The Remarkable Life And Career Of A Trailblazer